Definitions
Blockchain was first proposed in 2008 and implemented in 2009 (https://bitcoin.org/bitcoin.pdf)
Blockchain = a public ledger + transactions are stored in a list of blocks
Security is implemented using Asymmetric cryptography
Ledger consistency is implemented using distributed consensus algorithms (proof of work, or, proof of stake)
The typical digital signature algorithm used in blockchains is the elliptic curve digital signature algorithm
A
cryptocurrency wallet, comparable to a bank account, contains a pair of
public and private cryptographic keys. A public key allows for other
wallets to make payments to the wallet's address, whereas a private key
enables the spending of cryptocurrency from that address.
The
cryptocurrency itself is not in the wallet. In case of bitcoin and
cryptocurrencies derived from it, the cryptocurrency is decentrally
stored and maintained in a publicly available ledger called the
blockchain
Taxonomy of blockchain systems
Consensus
In Blockchain, there is no central authority that ensures ledgers on distributed nodes are all the same. Consensus algorithms are used to ensure ledgers in different nodes are consistent:
- Proof of work: if a node wants to publish a block of transactions, a lot of work has to be done first:
- Each node of the network is calculating a hash value of the block header
- The consensus requires that the calculated hash must be equal to or smaller than a certain value called "Target"
- The block header contains a "Nonce" and miners would change the nonce frequently until getting a valid hash value.
- Once node reaches the target value, it broadcast the block to other
nodes to confirm the correctness of the hash value and append this new
block to their own blockchains
- Proof of stake: only "reputed" nodes can create bocks: Reputation is often the coin amount owned by a miner.
- Miners have to prove the ownership of the amount of currency (stake size).
- Using only PoS leads to unfairness between miners (i.e. richest miner endup being monopoly)
- To avoid unfairness, PoS is combined with other strategies
- Such strategies are: Lowest hash value. Coin age based selection (older and larger sets of coins have a greater probability of mining next block).
- Byzantine fault tolerant: Consortium/private ledgers, voting consensus.
- Every node has to be known by all the network
- A block is created in a round.
- A node is candidate for a round if it has received votes from over 2/3 of all nodes.
- Ripple: Aristocratic approach.
- Only predefined nodes (called servers) participate on consensus
- A new block is added to the ledger if >80% of servers agreed on it.
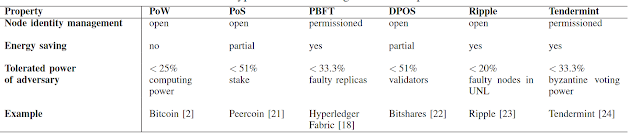
Consensus Algorithms Comparison
Block mining scenario
Foundations
Peer 2 Peer Network
Public-Private keys cryptography
Consensus protocols
Hash function properties:
- Collision free
- Hiding (irreversibly)
- compact (fixed-size)
Hash pointers used to guarantee that no data is tempered on a data structure (e.g linked list, binary tree).
Digital signature:
- Only you can sign
- Anyone can verify
- A signature cannot be forged (e.g cut-pasted from one document to another)
Ledger (i.e. BlockChain)
A mathematical structure for storing data in a way that is nearly
impossible to fake. It can be used for all kinds of valuable data.
It’s
a new way of answering an old question: how can we create enough trust
between one another to peacefully exchange something of value?
Application:
- Account-to-Account digital cash transfer: Alice sends an amount to Bob (e.g. Bitcoin)
- Smart contract digital cash transfer: someone stores a program -
called smart contract - in Blockchain. That program triggers to transfer
to a target account when conditions met)
Blockchain implementation
BitCoin (2009, Value store, C++)
Ethereum (2015. Open source. Smart contract) (Supported by Microsft)
Hyperledger (Open source, Java golang)(Supported by IBM, Linux foundation)
Corda (Open sourde, Haskell)
In Bitcoin jargon, BTC called cryptocurrency
In Ethereum jargon, ETH called Token
No cryptocurrency in Hyperledger, only smart contract?
Smart
contract (SC): make an agreement between a seller and a buyer to exchange
any commodity with value, more general than money transfer
Issues with SC :
- Oracle problem: when it comes to sell physical Objects via SC, a trusted authority (Oracle) is needed to verify the Object life cycle in both world: Real (physical) and Virtual (Blockchain). In general, no external data from the outside world can be brought into the
decentralized systems without trusting a third party as an oracle
Blochian scalability
Issue regarding public Blockchain: transaction processing scalability.
Possible solutio:
- Off-chain state channels : a mechanism by which Blockchain work get conducted off of the Blockchain.
- Sharding: transactions are directed to different nodes depending on which shards they affect. Each shard only processes a small part of the state.
- Plasma: a series of contracts that run on top of a root blockchain. The root blockchain enforces the validity of the state in the Plasma chains using “fraud proofs”
Wallet generation
Here is how Bitcoin, for example, wallet is created:
- generate ECC key pair (check here: https://github.com/lzbair/security/tree/master/ecc)
- Create a WIF (Wallet Interchange Format) by encoding the private key using a Base58. This is your secret key.
- Create your public address:
- Take public key and
compress it. public key compression means keeping only the x-coordinate,
y-coordinate is removed since it's calculable from the ellipiic curve
equation.
- Apply successive hash functions: SHA256 and RIPEMD160.
- Create a checksum for the c value.
- Concatenate hash value with it's checksum, and encode all in base58.
Questions
- Background: What's money? Currency? Exchange?
- Who can create a transaction? --> the holder of private key (wallet)?
- How a transaction is validated? for example a fake private key, or a wallet without credit
- Does transaction validation occurs during the process of block creation?
- How invalid blocks are detected and removed from the blockchain?
- Centralized vs Decentralized Exchange?
- How it works : Cloud Blockchain, Mining as a Cloud Service
- How to develop distributed application (dApps) using Ethereum / Hyperledger?
Bibliography
https://www.springer.com/gp/book/9783030030346
https://www.researchgate.net/profile/Hong-Ning_Dai/publication/318131748_An_Overview_of_Blockchain_Technology_Architecture_Consensus_and_Future_Trends/links/59d71faa458515db19c915a1/An-Overview-of-Blockchain-Technology-Architecture-Consensus-and-Future-Trends.pdf
https://www.amazon.com/Computer-Internet-Security-Hands-Approach/dp/1733003924